Taiwan AI Cloud's secure, compliant, and autonomous AI
Empowering enterprises to establish data sovereignty
Taiwan AI Cloud ensures data sovereignty and privacy security through multi-layered cybersecurity protection mechanisms and international certifications, providing secure and compliant one-stop AI Foundry Service.
In the AI 2.0 era, we help enterprises quickly adopt and deploy their own AI models, achieve technological autonomy, promote the application of AI, and enhance market competitiveness.
Secure AI
Compliant AI
Sovereign AI
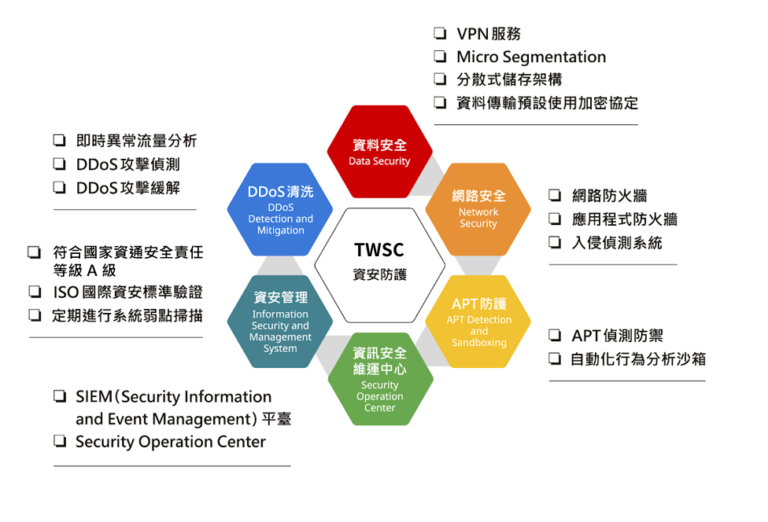
Secure AI — Balancing data protection and privacy for users and organizations
Data Security Data Security
- Micro Segmentation: Implements network segmentation for virtual hosting to prevent unauthorized data access.
- Distributed storage architecture: ensures data integrity and high availability.
- Data encryption: Enhance data security and protect sensitive data with passwords.
Cybersecurity Network Security
- Network firewall: For connections from the network layer to the application layer, a high-performance firewall performs access control and traffic management.
- Intrusion Detection System: Real-time detection and identification of network threat characteristics, detection of malware and hacker behavior to maintain platform security.
APT protection APT Detection and Sandboxing
- APT Detection and Prevention: Build an automated behavior analysis sandbox to analyze intercepted malware and detect botnets and potential APT connection activities.
- Integrate the information security operations center and send APT attack warnings.
Information Security Maintenance Center Security Operation Center
- Establish a SIEM (Security Information and Event Management) platform to collect and analyze the correlation of logs from heterogeneous devices.
- The information security maintenance center monitors network traffic and issues alerts and reports on cybersecurity incidents in response to threat behaviors.
Cybersecurity Management Information Security and Management System
- Multiple ISO international cybersecurity standard certifications: It has ISO 27001:2013 Information Security Management System, ISO 27017:2015 Cloud Service Information Security, ISO 27018:2014 Personal Privacy Data Protection and other cloud security and international cybersecurity certifications. It also continuously strengthens its internal cybersecurity control capabilities every year to help users build a safe and controllable environment.
- It meets the requirements of the Information and Communications Security Management Act, which classifies information and communications security responsibility level as Level A for specific non-governmental organizations.
DDoS cleaning DDoS Detection and Mitigation
- Monitor the Netflow data of external routers to analyze abnormal traffic in real time and detect potential DDoS attacks.
- We provide DDoS protection services and effectively mitigate the impact of DDoS attacks on the platform through a traffic diversion and cleaning mechanism.
Sovereign AI — Infrastructure and platform services that comply with international and governmental security and availability standards
Supports multiple security standards and certifications to meet customer compliance requirements.
Professional cybersecurity protection with high security
International standard certified high security
High standards of data center operation
Obtaining DCOS® (Data Center Operations Standard) Level-4 certification represents a high standard of operation and reliability for data centers, ensuring users have access to trusted data center management and secure maintenance services.
High and stable service quality commitment
We provide service tier agreements (SLAs) and uninterrupted, high-quality service to ensure the stability and quality of service for our customers in the cloud.
Two-factor authentication for enhanced protection upon login
Global Certification and Verification







ISO 9001
ISO 27017
ISO 27018
ISO 50001
ISO 27001
ISO 20000
Taiwan Certification and Verification


Other countries' certifications and verifications


Sovereign AI — Users have control over model selection, operating environment, and content fine-tuning.
Collaborate with ecosystem partners to create comprehensive high-security solutions and protect user data and service security.
Choice of diverse open source and traditional Chinese enhanced large model
Data is a critical resource for enterprise operations and AI training. Taiwan AI Cloud not only provides an ever-expanding range of controllable open-source models, but also a Traditional Chinese-enhanced FFM Formosa Foundation Models, operating in a secure and privacy-protected environment. This helps users take control of their data assets, strengthen data governance, and ensure security and compliance. Through Taiwan AI Cloud, enterprises can confidently develop and deploy generative AI applications, driving innovation and sustainable growth.
Deepen strategic partnerships and expand the ecosystem
Taiwan AI Cloud continues to work closely with key strategic partners such as ASUS Group, NVIDIA, and Trend Micro to co-create trustworthy and highly secure solutions. Examples include ASUS's All in AI initiative to meet the needs of AI-driven applications, including edge, inference, and generative AI; OneAI's one-stop MLOps service to assist in digital healthcare R&D, using NVIDIA FLARE™ to prevent the sharing of confidential data; and collaborating with Trend Micro to develop secure applications to help users address security concerns in the deployment and use of large models, resolving security and legal compliance issues related to large model development, use, and deployment.