TWSC Cloud Object Service (COS) is an object storage system compatible with Amazon S3 and supports encrypted uploads and downloads. Users can access it through...s3cmd setpolicy Commands or S3 Browser Graphical interfaces and other tools can be used to set access rules for storage, allowing only permitted source IPs to access it, thus enhancing the security of users' storage and files. This article will teach you how to use s3cmd and S3 Browser to restrict the source IPs that can access storage.
Preparatory work
1. Establish TWSC COS
Please refer to the setup instructions.Create and delete storage
2. Connect TWSC COS
For instructions on installing s3cmd and S3 Browser, and for configuring the connection to the COS storage, please refer to the following documents.
3. Confirm the COS storage name and the allowed source IP addresses.
- You can (1) through
s3cmd lsCommand (2) S3 Browser: View all public/private storage names - Confirm that you allow the use of the source IP address of this storage.
Detailed Steps
Step 1. Edit JSON rule file
The following is a sample JSON rules file, allowing only (AllowThe source IP is 203.145.219.99/32 right your-bucket-name Reading and downloading from storage (s3:GetObjectThe action of )
{
""Version"": "2012-10-17",
""Statement"": [
{
""Effect"": ""Allow"",
""Principal"": "*",
""Action"": ""s3:GetObject"",
""Resource"": ""arn:aws:s3:::your-bucket-name/*"",
""Condition"": {
""IpAddress"": {
""aws:SourceIp": "203.145.219.99/32"
}
}
}
]
}
Please replace the following items in the rule file with content that applies to you:
your-bucket-nameReplace with your storage name203.145.219.99/32Replace it with the range of IP addresses you allow access to.- For more information on JSON configuration files, please refer to [link/reference].This file
Step 2. Set JSON rules for the bucket
-
s3cmd
- Create a rule file named "policy" (the file name can be defined by yourself), and enter the editing screen:
nano policy.json - Copy and paste the Step 3 JSON configuration file content.
- Create a rule file named "policy" (the file name can be defined by yourself), and enter the editing screen:
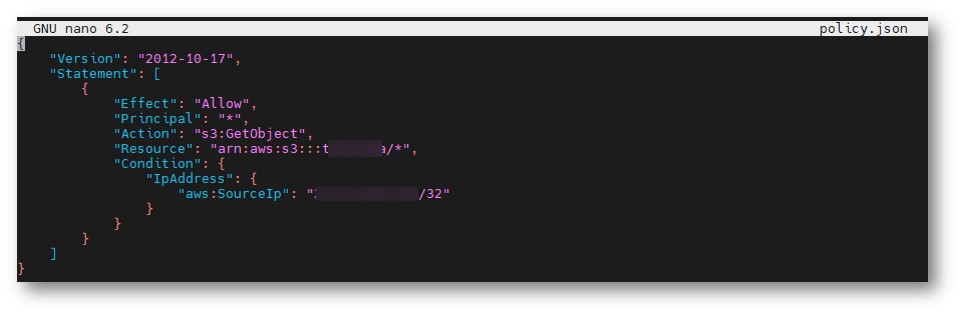
-
- Click
Ctrl + O,EnterSave and confirm the configuration file name - Click
Ctrl + XLeaving the editing screen - Execute the following commands to set the rules.
your-bucket-namePlease replace the name with your storage device name to complete the setup successfully.s3cmd setpolicy policy.json s3://your-bucket-name
- Click
-
S3 Browser
- Right-click on the bucket > Select Edit Bucket Policy
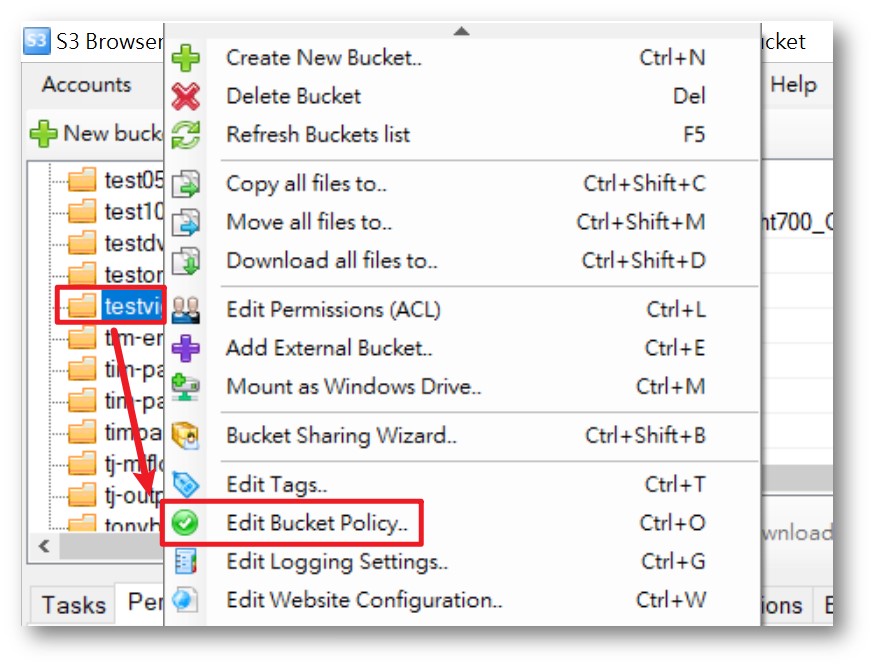
-
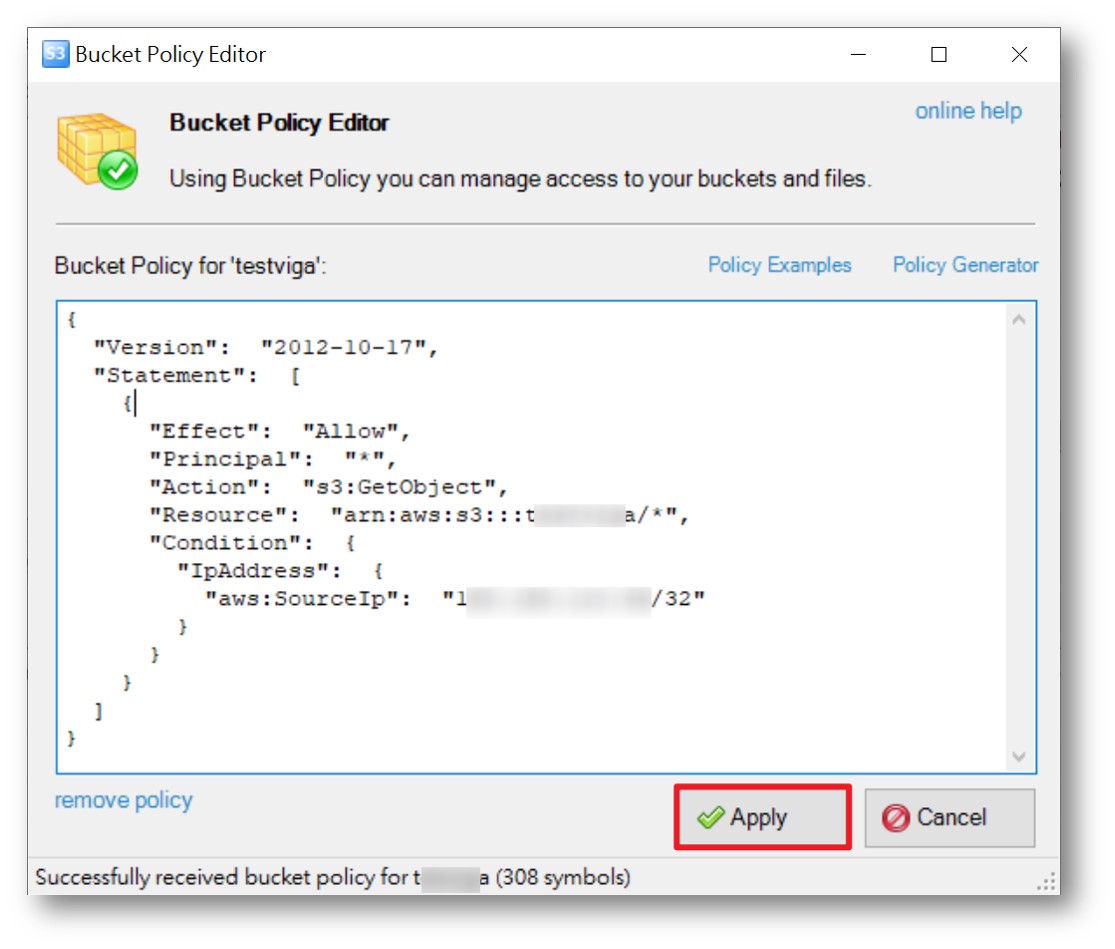
- Copy and paste the Step 1 JSON configuration file content > click Apply to successfully configure it.
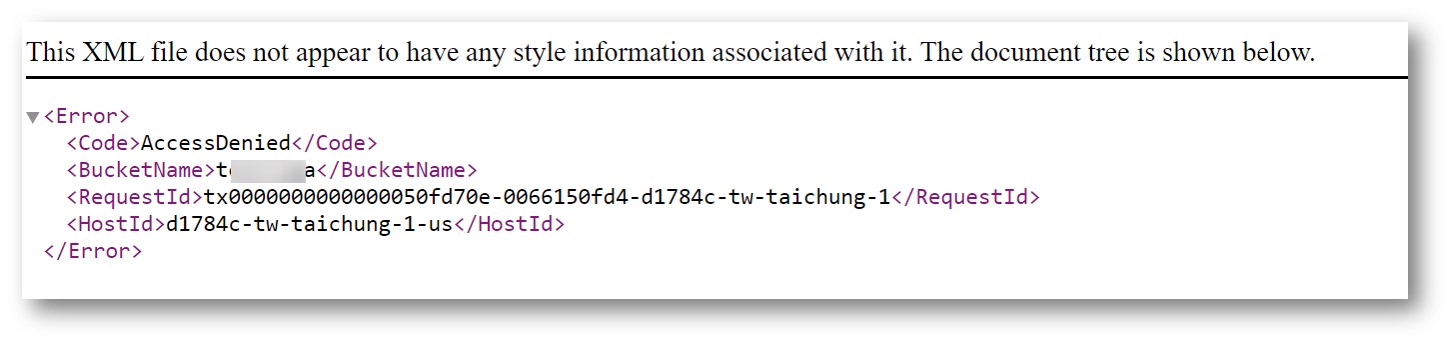
Step 3. Test: Unauthorized IPs cannot view files.
- COS file URL:https://your-bucket-name.cos.twcc.ai/your-file-name.extention
your-bucket-nameChange to bucket nameyour-file-name.extentionReplace with [filename.extension]
- If the URL that connects to the file is from an IP range other than that set in Step 2, the file content cannot be viewed; only an "Access Denied" message will be displayed. Confirm that the rule settings were successful!